Troubleshoot SSL/HTTPS key generation
Verify certificate path in Windows
If you are getting errors with your new SSL certificateSSL certificates are small data files that digitally bind a cryptographic key to an organization’s details, such as a company's domain name, your company name, your address, your city, your state and your country. When installed on a web server, it activates the padlock and the HTTPS protocol (over port 443) and allows secure connections from a web server to a browser. When a browser connects to a secure site it retrieves the site's SSL certificate and checks that it has not expired, it has been issued by a Certification Authority the browser trusts, and that it is being used by the website for which it has been issued. If it fails on any one of these checks the browser will display a warning to the end user letting them know that the site is not secured by SSL. SSL certificates can be either self-signed or CA signed. one of the first things to check is that the intermediary certificates have been loaded correctly. You can do this via Internet Explorer, and every other modern web browser, the steps differ slightly.
Load Internet Explorer and visit the HTTPs URL for your PaperCut MF server then click the padlock near the URL bar as below.
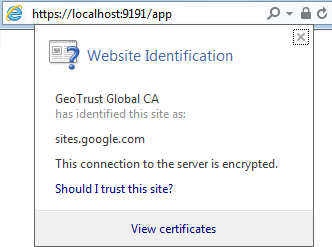
Then click View Certificates and navigate to the Certificate Path and verify it is correct.
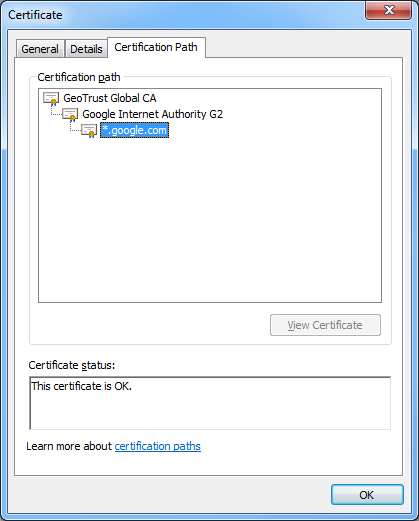
If the path is invalid, confirm that you have correctly inserted the required intermediary certificates. See Creating and installing a purchased SSL Certificate
Verify certificate path via command line with OpenSSL
A quick way to easily validate the chain output by the server. This requires either Linux or Cygwin with openssl’s packages installed:
openssl s_client -connect [server]:[port] -crlf
Once the text has been output, type in:QUIT
For example, a self-signed certificate looks like this:
openssl s_client -connect localhost:9192 -crlf
CONNECTED(00000003)
depth=0 C = Unknown, ST = Unknown, L = Unknown, O = Unknown, OU = Unknown, CN = print-server
verify error:num=18:self signed certificate
verify return:1
depth=0 C = Unknown, ST = Unknown, L = Unknown, O = Unknown, OU = Unknown, CN = print-server
verify return:1
--- Certificate chain
0 s:/C=Unknown/ST=Unknown/L=Unknown/O=Unknown/OU=Unknown/CN=print-server
i:/C=Unknown/ST=Unknown/L=Unknown/O=Unknown/OU=Unknown/CN=print-server
---
An example of a certificate that uses a chain, note the 0, 1, 2 and how the i: (issuer) matches with the s:(subject): of the next certificate.
$ openssl s_client -connect www.google.com:443 -crlf
CONNECTED(00000003)
depth=2 C = US, O = GeoTrust Inc., CN = GeoTrust Global CA
verify error:num=20:unable to get local issuer certificate
---
Certificate chain
0 s:/C=US/ST=California/L=Mountain View/O=Google Inc/CN=www.google.com
i:/C=US/O=Google Inc/CN=Google Internet Authority G2
1 s:/C=US/O=Google Inc/CN=Google Internet Authority G2
i:/C=US/O=GeoTrust Inc./CN=GeoTrust Global CA
2 s:/C=US/O=GeoTrust Inc./CN=GeoTrust Global CA
i:/C=US/O=Equifax/OU=Equifax Secure Certificate Authority ---
ERR_SSL_VERSION_OR_CIPHER_MISMATCH & SSLHandshakeException: no cipher suites in common
If you receive an error message of ERR_SSLSecure Sockets Layer (SSL) is the standard security technology for establishing an encrypted link between a web server and a browser. This link ensures that all data passed between the web server and browsers remain private and integral. The protocol uses a third party, a Certificate Authority (CA), to identify one end or both end of the transactions. To be able to create an SSL connection a web server requires an SSL certificate. When you choose to activate SSL on your web server you will be prompted to complete a number of questions about the identity of your website and your company. Your web server then creates two cryptographic keys - a Private Key and a Public Key._VERSION_OR_CIPHER_MISMATCH in your web browser or notice SSLHandshakeException: no cipher suites in common in the [app-path]\server\logs\server.log it is likely that the certificate chain is not complete or the SSL certificate is in the wrong alias in the key-store. See Check that the correct Alias has been used in the keystore to confirm the correct alias is in use.
Check that the correct Alias has been used in the keystore
PaperCut MF is configured to use the alias "jetty". If your SSL certificate is installed into another alias it will not load correctly. To confirm run the following command:
keytool -list -v -keystore my-ssl-keystore-20151217
Enter keystore password: [password]
Keystore type: JKS
Keystore provider: SUN
Your keystore contains 1 entry
Alias name: jetty
Creation date: 17/12/2015
Entry type: PrivateKeyEntry
The PrivateKeyEntry needs to be present in the jetty Alias. If it has been imported into another alias, you can use keytool.exe to rename it. See Extended keytool.exe usage
