PaperCut NG normally relies on the underlying operating system and the associated print queues to perform authentication. For example, in normal operation, a user logs into a workstation using a domain/network level authentication method such as a username and password. The print queues also use this authentication and PaperCut NG can trust the supplied identity. However in some network environments, relying on network level authentication may either not be possible, or may not be reliable. Common examples include:
All users log in with a common generic username and password meaning that it's not possible to distinguish between users.
A print queue that does not enforce authentication.
For a detailed explanation of print authentication, please Chapter 26, Print Authentication.
Popup Authentication matches the source IP address of the print job with the user confirmed to be operating from the popup client IP address. The workflow is as follows:
The user initiates a print job to a server-hosted, PaperCut NG-managed, queue (printer) via unauthenticated print protocol.
The print job arrives in the print queue and because of the unauthenticated protocol, the username cannot be trusted.
PaperCut NG uses the job's source IP address to determine the PaperCut NG popup client it should contact for authentication.
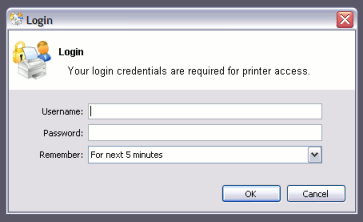
The user is prompted to enter their username and password, which are then verified against PaperCut NG's configured directory source. If the credentials are correct, the user is considered authenticated at that client.
The print job is attributed to the authenticated user.
Depending on configuration, the server may remember the association between the IP address and the authenticated user for a period of time.
Some real life examples include:
Some student labs are set up so everyone logs in using a generic username and password. For example, username: student, password: student. This is common in Apple Mac labs, where enabling multi-user authentication is complex and can often prevent selected applications from running correctly.
The Line Printer Daemon print protocol, often used in UNIX environments, is a non-authenticated system. The username associated with the print jobs is passed through to the print queue, however the name is not verified and can easily be forged. An extra level of authentication is required.
CUPS, the modern print system often used on Linux, Apple Mac and some Unix systems, is often implemented in a non-authenticated fashion. Although CUPS can support authentication, technical considerations such as the inability to interface with Active Directory domain authentication often prevent its use.
Mac OS X server use the CUPS print system. Current Apple implementations prevent administrators from enabling CUPS authentication. This is not usually a problem in an environment where logins can be controlled at individual workstation level. It does however pose a problem if users have local admin access - for example, individual owned laptops. PaperCut NG popup authentication provides a way to work around the non-authentication issue.
More information, including a discussion of platform specific issues is available in Chapter 26, Print Authentication.
Popup authentication is often required on Mac networks supporting a mix of lab systems authenticated via a directory service and unauthenticated laptop systems. Advanced administrators may wish to review the section called “Eliminating PopUp Authentication via Mac Login Hook” to streamline login on the secured lab systems.
PaperCut comes with an iPad / iOS app that provides popup authentication and other functionality. For more information see the section called “iOS Printing (iPad & iPhone)”.
As a general rule, Popup Authentication should only be used in low-volume, low-complexity scenarios when Protocol-Level Authentication has been ruled out. By its design, Protocol-Level Authentication is always the most secure and hence this is the reason why it is used in Windows and authenticated protocols such as HTTP, SSH or Novell's iPrint protocol.
A good example of a situation where Protocol-Level Authentication is not ideal would be a public-access PC in a library set to auto-logon as the insecure, generic account "public". In this case the Protocol-Level Authentication is passing through the insecure user of "public". PaperCut NG's client software and IP address authentication can overlay these insecure user credentials and request authentication from the user at the time of print via a popup.
The following is a general guide to factors your System, Network and Security teams should consider when implementing Popup Authentication:
IP address changes should be minimized. If you are using DHCP, consider the lease time as well as the re-use rate of IP address and DNS scavenging timeouts.
Do not use any form of NAT between the clients and print server. NAT will obscure the IP address seen by the server.
Consider the authentication session time (TTL - Time To Live) options offered to your users. This is detailed further in the Popup Authentication configuration page of the manual. TTL settings are a trade-off; the shorter the time, the smaller the window of mismatch, but the greater the inconvenience to the user. There is no one-size-fits-all answer, this must be taken on a site-by-site basis.
Ensure that hostnames can be resolved to IP addresses, both from the client and server. In some situations, hostnames may be reported instead of IP addresses, and resolution results are key to correct behaviour.
Any machine relying on Popup Authentication must have the PaperCut NG client running at all times for printing from that workstation to function.
Awareness of IP address spoofing. Large sites will often actively monitor this and/or endeavour to prevent it, as IP address spoofing is something that affects network application security in general.
Always reconsider your choice of Popup Authentication. Protocol-Level Authentication may become viable with changes in technology, infrastructure or internal procedure.
Popup Authentication is not a viable solution for simultaneous multi-user systems, such as Terminal Server or Citrix, as multiple users will be reported from a single IP address.
In 2012 one major university user of PaperCut NG in the USA were using Popup Authentication to support authentication on print jobs issued via the LPR protocol (for Unix desktop systems). This setup had been in place successfully for 5 years with no reported problems. The site's networking team (independent of the server team responsible for PaperCut NG's management) decided to make a few network infrastructure changes and enabled NAT for some subnets. Thhis caused a subtle set of authentication issues that took a number of days to detect and diagnose. During this time some jobs were incorrectly attributed.
The following sections cover how to enable popup authentication on either the user account level or the print queue level.
The following notes explain how to enable popup authentication when a user logs in under a generic
user account - for example, student.
Add the account to the domain called
student. You may already have such as account set up.Perform a or print a job from this account so the username is listed in PaperCut NG
Select the generic user and set the account to a zero balance and a restricted status. This will ensure that users can't charge against this account.
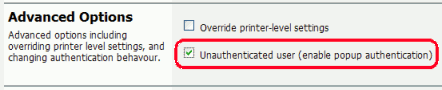
Check the Unauthenticated option and click on the button to save the changes.
Install client software on workstations. See the section called “User Client” for details.
When a user logs in as the generic
student, they will be prompted for their domain level username and password.
The following notes explain how to enable popup authentication when a user attempts to print to a non-authenticated printer such as one hosted via an LPR/LPD queue or a CUPS print queue:
Add the printer to the system as normal. Perform a few test prints to ensure the printer is functioning and tracking as expected.
Log into PaperCut NG and check the Unauthenticated option under the relevant print to enable the popup authentication.
Install the client software on any workstation that will print to this printer. See the section called “User Client” for details.
When a user attempts to print to this printer, they will be prompted for their username and password.
When running in popup authentication mode, the client makes available a number of additional options including:
Logout
Login as another user
The Logout option is available on Windows via either the right-click option on the task try icon, or when running on Mac or Linux, via a right-click popup menu (Option Click) access via the icon on the balance window.
The Login as... option is made available if the client starts as an unauthenticated user. This option allows users to authenticate or quickly switch user identity.
The login box displayed to the user offers the choice of how long their authentication details should remain active. An administrator can control the options presented to the user by modifying the following system configuration keys. These configuration keys are edited under → →
| Config name | Description |
|---|---|
client.config.auth.ttl-values | A comma separated list of values to display in the popup authentication login box. Positive numbers represent the number of minutes to remember the authentication for.
The value of
The value of
The value of
The default is: |
client.config.auth.ttl-default-minutes | The default time-to-live value automatically selected when the login authentication window displays. |
client.config.auth.popup-on-startup-if-unauthenticated |
Determine if the client should request authentication when the
client starts if the operating system user is unauthenticated.
Set to |
Table 7.2. User Client Popup Config Keys
Important
User client tools that are already running will pick up changes made via the config editor the next time they are restarted.
Please see the section called “Using the Config Editor” to find out how to change config keys.